Checkpoint Firewall Services
Welcome to Cloud Sparkle – Your Trusted Checkpoint Solutions Partner
At Cloud Sparkle, we pride ourselves on being leaders in the realm of Check Point software technologies. With an unwavering commitment to delivering top-tier solutions, our team brings unparalleled expertise and experience in deploying a wide array of Checkpoint security solutions, empowering businesses to safeguard their networks and critical assets.
Our Check Point Services:
1. Comprehensive Deployment Solutions:
We specialize in the seamless deployment of Check Point’s suite of security solutions, including firewalls, VPNs, intrusion prevention systems, endpoint security, and more. Our team ensures a customized deployment that aligns perfectly with your organization’s security needs and infrastructure.
2. Expert Consultation and Customized Solutions:
Leveraging our extensive knowledge base and hands-on experience, we offer expert consultation to design tailored security architectures. We provide solutions that not only address existing vulnerabilities but also anticipate and mitigate future threats, ensuring robust protection against evolving cyber risks.
3. Cloud Security Solutions:
As cloud environments become increasingly pivotal in today’s digital landscape, we specialize in implementing Check Point’s cloud security solutions, offering seamless protection across hybrid and multi-cloud architectures. Our proficiency spans across CloudGuard, ensuring your cloud infrastructure remains secure and compliant.
4. Proactive Security Measures:
Our approach extends beyond mere implementation. We’re dedicated to ensuring your security posture remains robust by delivering proactive maintenance, support, and threat intelligence updates. Count on us for 24/7 monitoring, ensuring a swift response to emerging threats.
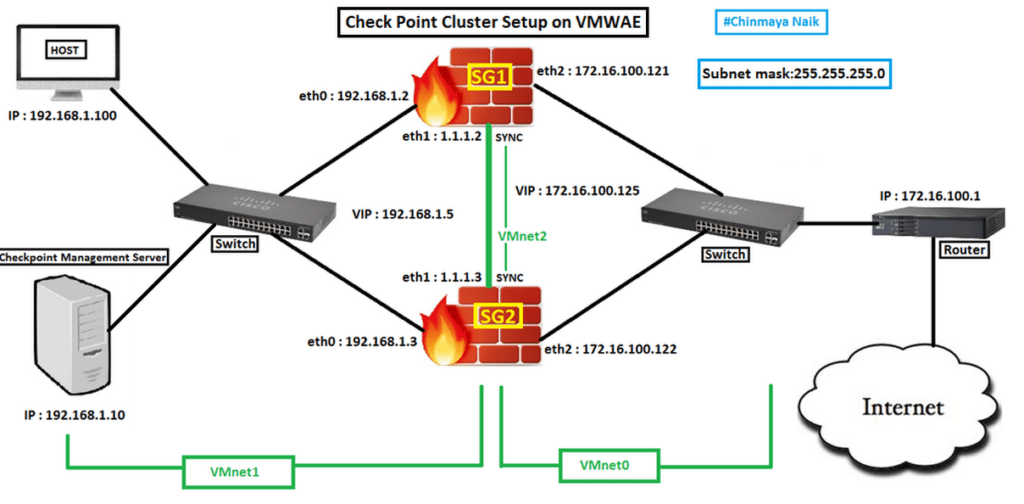
Checkpoint Cluster Deployment Diagram:
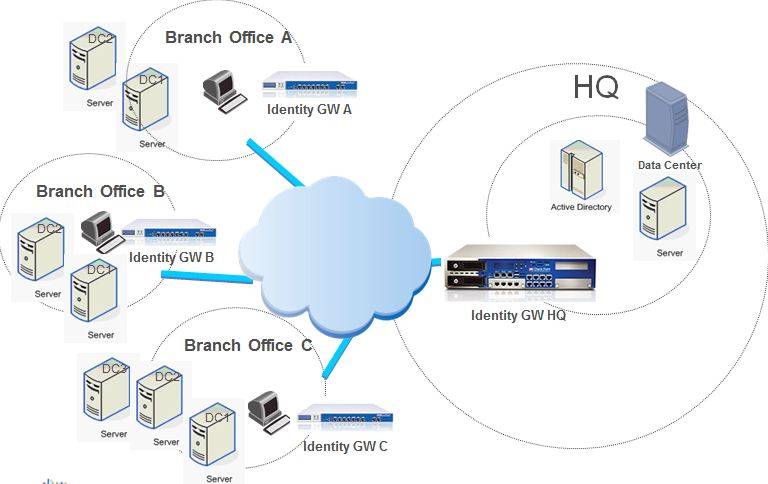
Checkpoint Largescale Deployment Diagram:
Why Choose Cloud Sparkle:
Certified Experts: Our team comprises certified professionals with extensive experience and in-depth knowledge of Check Point technologies.
Proven Track Record: With a history of successful deployments and satisfied clients, we’ve established ourselves as reliable and trusted partners in the cybersecurity domain.
Tailored Solutions: We understand that every business is unique. Hence, our solutions are tailored to address your specific security challenges and requirements.
Client-Centric Approach: Your security needs are our priority. We collaborate closely with you to comprehend your challenges and provide solutions that exceed your expectations.